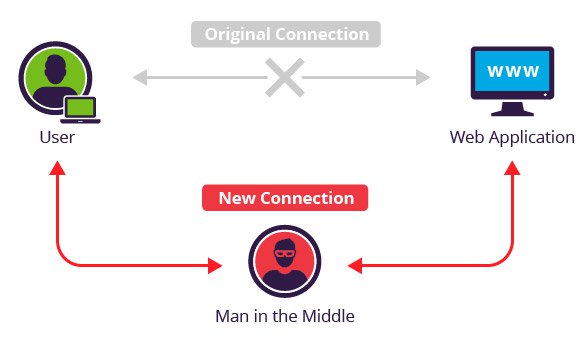
MITM Part 2 - Scan & Attack
This is the second part in our series of security/penetration testing/ethical hacking articles, continuing where we left off in part 1. This will be a slightly longer post, but stick with it and you’ll see just how easy it is. Introduction In this part of the series, we’re going to use our Kali based attacker’s machine to scan the local network and find our Windows target. We’ll then carry out an ARP Poisoning based MITM attack against it as we explained in part 1.